Attack Flow
Quick links
Obtaining IP Address | DoS attack | Phishing | Reverse-shell attack | Manipulating files
1. Obtaining Victim’s IP Address Through Phishing
-
Create an accound for a free website hosting service.
-
Extract the IP_Finder.ZIP (Source codes) and upload the two files ip.php and ip_log.txt to the root folder of your hosting account.
-
Rename the ip.php to index.php.
-
Set the permission to 777 on ip_log.txt.
The phishing email:
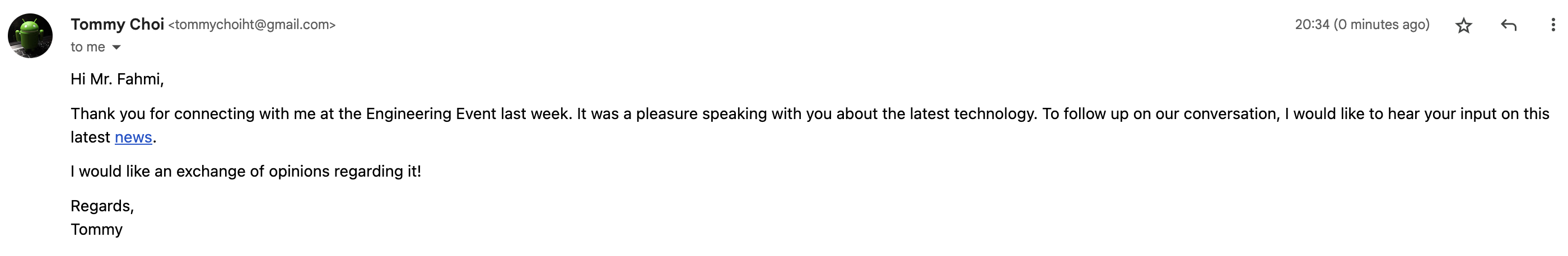
Hi Mr. Fahmi,
Thank you for connecting with me at the Engineering Event last week. It was a pleasure speaking with you about the latest technology. To follow up on our conversation, I would like to hear your input on this latest news.
I would like an exchange of opinions regarding it!
Regards,
Tommy
2. DDoS to a company’s computer to cause slow network traffic with LOIC
- Refer to this guide on how to launch the attack
3. Send a phishing email with the ‘Network Diagnostic Tool User Guide’ to offer a solution to the slow traffic
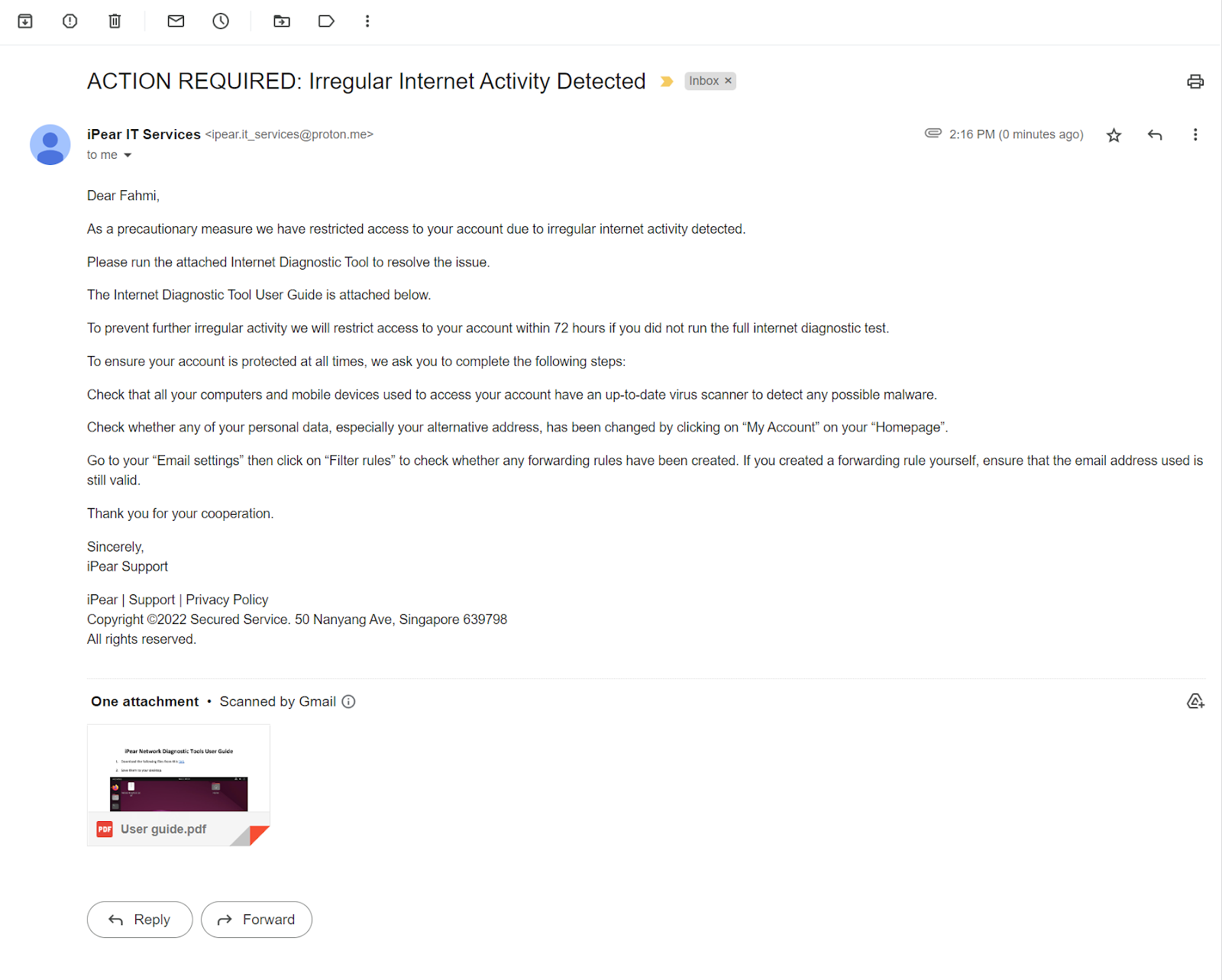
Subject: ACTION REQUIRED: Irregular Internet Activity Detected
Date: 19 Feb 2021 05:37:51 -0800
From: Security Notice it-services@support.ipear.comDear Fahmi,
As a precautionary measure we have restricted access to your account due to irregular internet activity detected.
Please run the attached Internet Diagnostic Tool to resolve the issue.
The Internet Diagnostic Tool User Guide is attached below.
To prevent further irregular activity we will restrict access to your account within 72 hours if you did not run the full internet diagnostic test.
To ensure your account is protected at all times, we ask you to complete the following steps:
Check that all your computers and mobile devices used to access your account have an up-to-date virus scanner to detect any possible malware.
Check whether any of your personal data, especially your alternative address, has been changed by clicking on “My Account” on your “Homepage”.
Go to your “Email settings” then click on “Filter rules” to check whether any forwarding rules have been created. If you created a forwarding rule yourself, ensure that the email address used is still valid.
Thank you for your cooperation.
Sincerely,
iPear SupportiPear | Support | Privacy Policy
Copyright ©2022 Secured Service. 50 Nanyang Ave, Singapore 639798
All rights reserved.
4. Gain access to the computer and navigate through the computer’s directories
- for technical details refer to this guide
5. Upload whatever files we want to file.io
- Refer to this guide on how to upload and download files